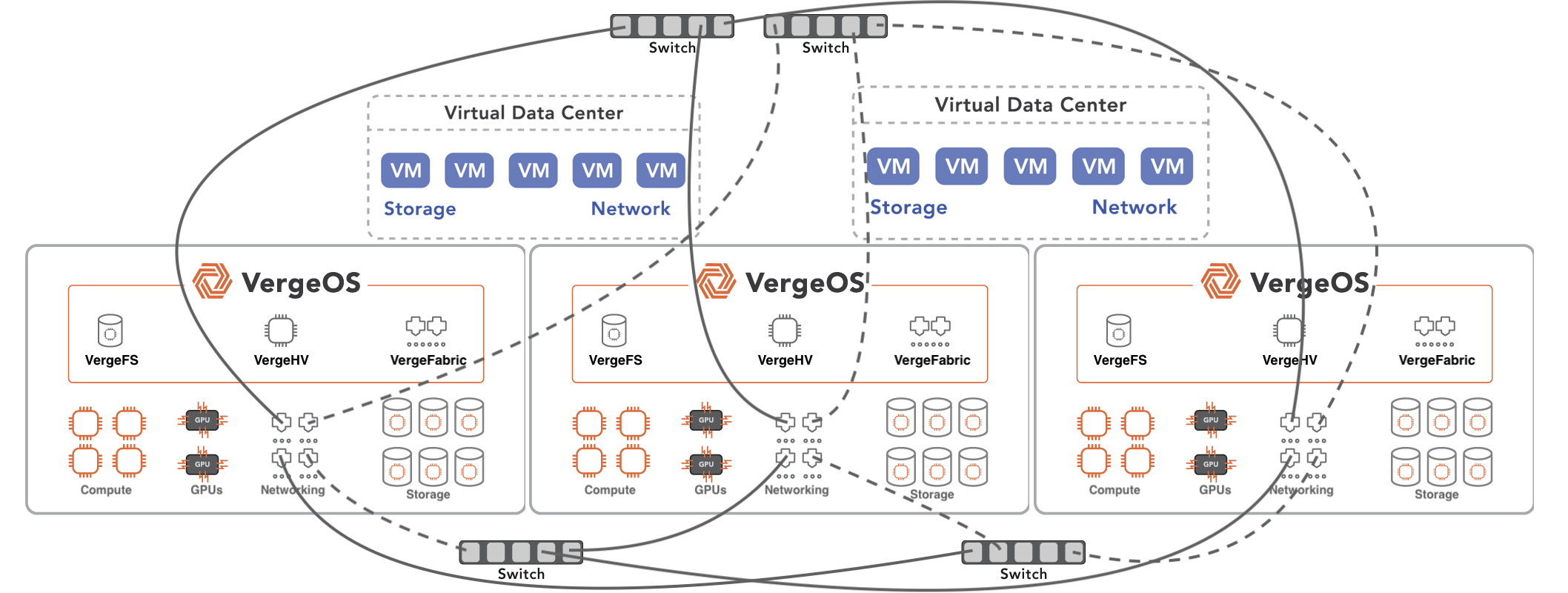
A double-protected VMware alternative allows organizations to lower licensing expenses and enhance their data resilience. With the rise of infrastructure threats and the need for continuity of operations, IT should leverage this infrastructure shift to boost its recovery capabilities from accidental file deletions, server or drive failures, site disasters, and long-term data retention needs.
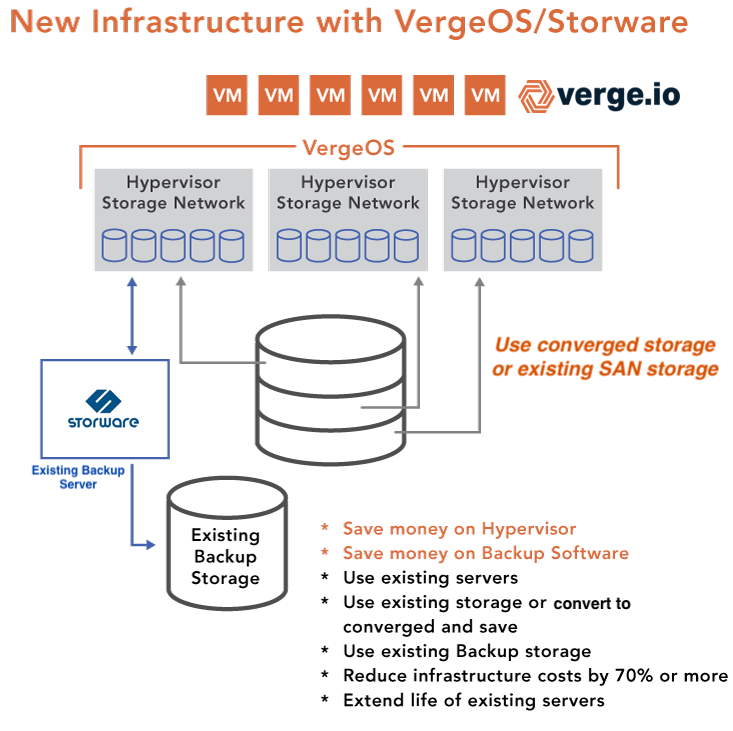
A robust VMware alternative must provide two layers of protection: real-time infrastructure resilience and long-term data protection. VergeIO and Storware work together to create a double-protected solution, combining real-time safeguards like ioGuardian, ioClone (snapshots), and ioReplicate with long-term retention and archival capabilities provided by Storware Backup and Recovery.
This approach delivers the strongest data protection strategy and allows IT teams to leverage existing server and backup storage hardware, reducing costs and eliminating the need for rip-and-replace upgrades.
First Layer of Protection: Built-in Infrastructure Resiliency
Many VMware alternatives rely heavily on third-party backup solutions for protection, leaving gaps in immediate recovery and real-time failure resilience. A double-protected VMware alternative must first integrate infrastructure-native data protection that ensures data availability without relying on backups for everyday failures.
ioGuardian: Continuous Failure Detection and Recovery
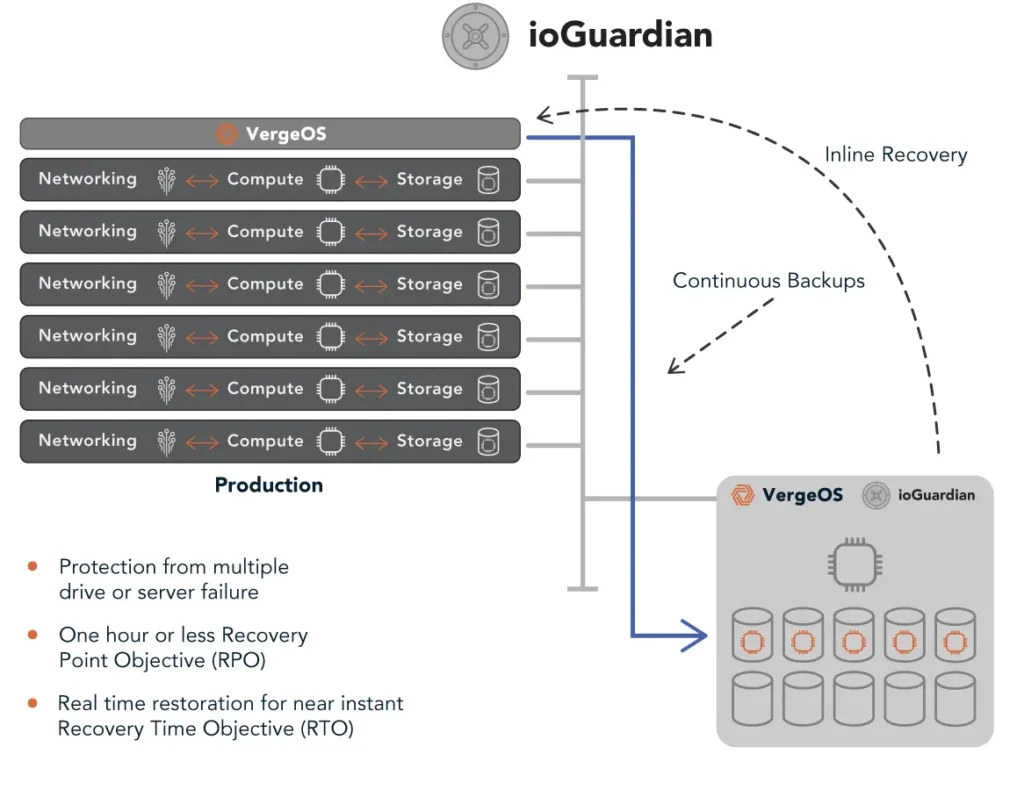
The foundation of VergeIO’s built-in resiliency is ioGuardian, which proactively monitors infrastructure health and automatically reroutes workloads in the event of drive or node failures. Unlike traditional instant-recovery solutions that require IT intervention, ioGuardian provides real-time, automated protection that keeps applications running without delays or downtime. It also protects against multiple simultaneous drive failures, ensuring data remains accessible even in worst-case scenarios.
ioClone: Instant, Space-Efficient Snapshots
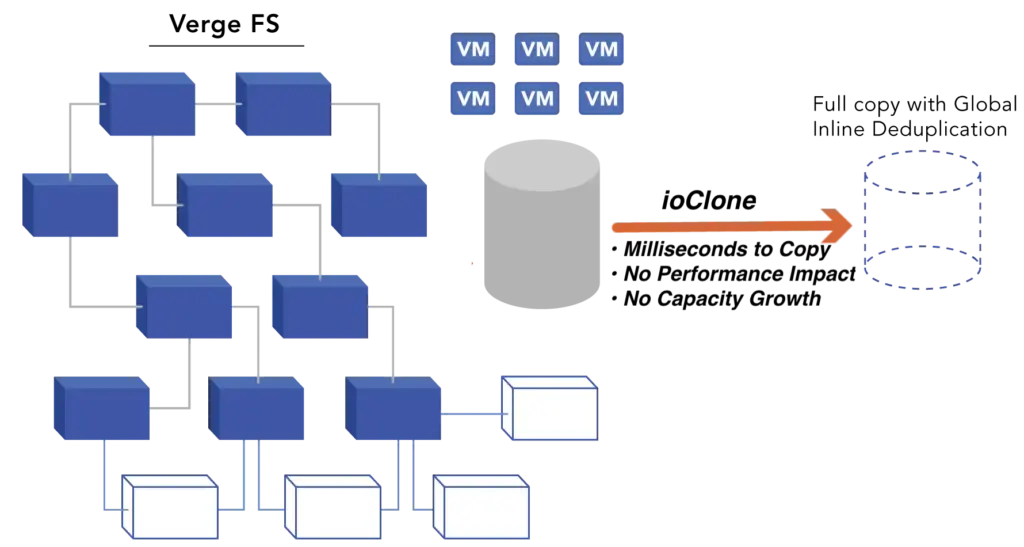
Snapshots are a critical component of an effective data resilience strategy, but most legacy HCI and VMware solutions create performance bottlenecks when snapshots accumulate. VergeIO’s ioClone snapshots eliminate this issue by providing instant, space-efficient, performance-neutral snapshots that IT can use to recover from accidental deletions and system corruption quickly. Snapshots can even be used to recover from ransomware attacks because they are read-only from inception.
ioReplicate: Multi-Site Data Resiliency
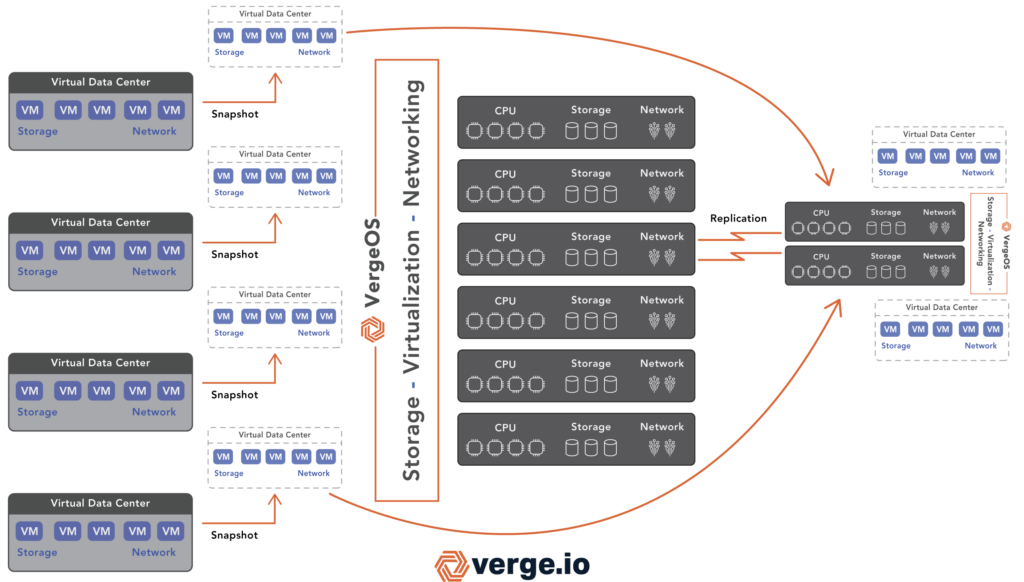
VergeIO offers ioReplicate, an efficient, WAN-optimized replication engine that enables real-time or scheduled replication to offsite locations for organizations needing geo-redundancy. This ensures that even in the event of a primary site failure, IT teams can rapidly failover and restore operations from a secondary location.
Global Inline Deduplication
VergeOS features integrated global inline deduplication, the foundation for both ioClone and ioReplicate. This technology decreases storage consumption by ensuring that unique data blocks are written, greatly enhancing efficiency. Removing redundant data globally improves storage performance and maximizes available capacity, making snapshots and replication operations even more cost-effective.
Second Layer of Protection: Long-Term Data Retention
A double-protected VMware alternative requires more than built-in resiliency and data availability in real-time. IT teams also need a long-term data protection strategy to defend against data corruption, cyber threats, and to meet compliance requirements.
Storware Backup and Recovery: Deep Integration with VergeIO
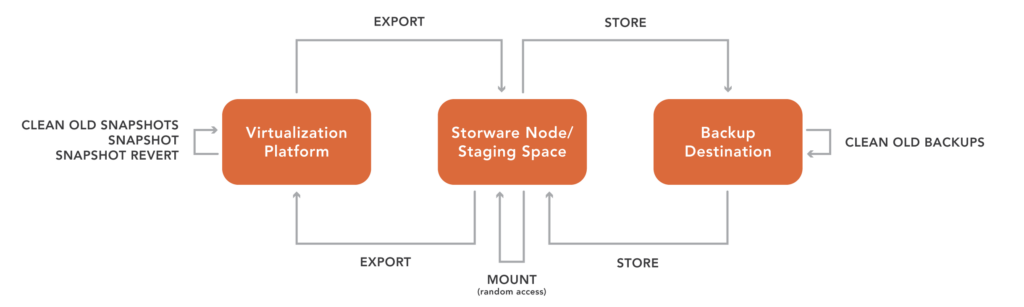
Storware extends VergeIO’s protection by offering long-term backup retention, compliance archiving, and multi-destination backup support, allowing organizations to meet regulatory and business continuity requirements. Unlike traditional backup solutions, Storware is directly integrated into VergeOS, enabling seamless backup of ioClone snapshots and leveraging VergeIO’s changed block tracking (CBT) for faster, storage-efficient backups.
To learn more about VergeIO’s and Storware’s Double Protection and to see it in action, watch our on-demand webinar, “Exit VMware, Retain Server and Backup Hardware.”
Use Existing Server and Backup Storage Hardware
VergeOS enhances flexibility by supporting a broad range of existing server hardware. With its intelligent resource allocation and ability to run on nearly any x86 hardware purchased in the last six years, IT teams can continue using their current infrastructure instead of refreshing everything simultaneously.
One of the most costly aspects of transitioning off of VMware is replacing backup infrastructure due to compatibility limitations with new platforms. Storware removes this concern by supporting a wide range of backup storage hardware, including:
- Existing NAS/SAN backup storage
- Object storage (on-prem and cloud-based)
- Backup appliances from vendors like Rubrik, ExaGrid, and Dell EMC
Storware: Keep Your Existing Backup Storage
Storware enables IT teams to continue using their existing backup storage infrastructure, eliminating the need to purchase new backup appliances. Whether organizations rely on on-premises storage or cloud-based repositories, Storware provides seamless backup and archival capabilities. This flexibility helps businesses reduce costs while ensuring backup operations remain efficient and secure.
ioOptimize: Extending Hardware Lifespan
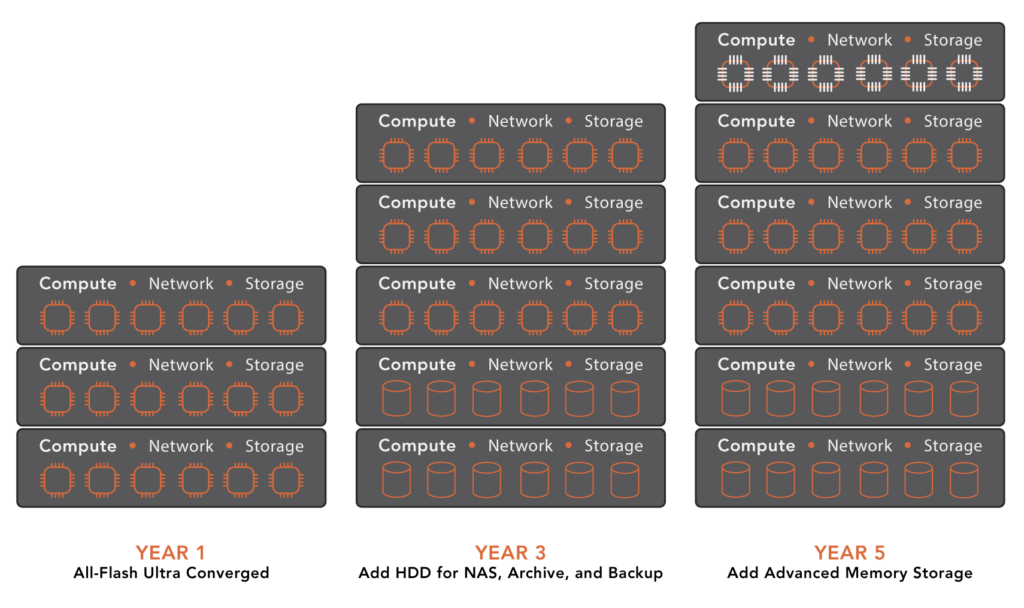
VergeOS includes ioOptimize, a technology designed to maximize the efficiency of existing hardware. By intelligently distributing workloads, optimizing storage, and reducing system overhead, ioOptimize allows organizations to extend the life of their current infrastructure while also improving performance. IT teams can repurpose aging servers and storage systems rather than retiring them early, ultimately reducing costs and making infrastructure refresh cycles more flexible.
The Most Data-Resilient VMware Alternative
VergeIO believes that data protection and resiliency is a shared responsibility. The combination of VergeIO and Storware creates the most resilient VMware alternative, delivering:
- Real-time failure detection and recovery with ioGuardian
- Instant, space-efficient snapshots with ioClone
- Multi-site data replication with ioReplicate
- Fast, storage-efficient backups with Storware’s CBT integration
- Long-term retention and archival capabilities using existing backup storage hardware
- Extended server lifecycle with ioOptimize
With VergeIO’s built-in resilience and Storware’s long-term data protection, IT teams can confidently transition from VMware without sacrificing security, availability, or infrastructure flexibility.
Conclusion
A VMware exit should not come at the cost of data protection or hardware flexibility. VergeIO and Storware provide a double-protected VMware alternative that delivers real-time resilience and long-term security, ensuring IT teams reduce costs, enhance uptime, and retain control over their infrastructure.
Organizations looking to exit VMware now have a cost-effective, highly available, and deeply resilient alternative that protects both today and into the future.