Simplifying Public Sector DR
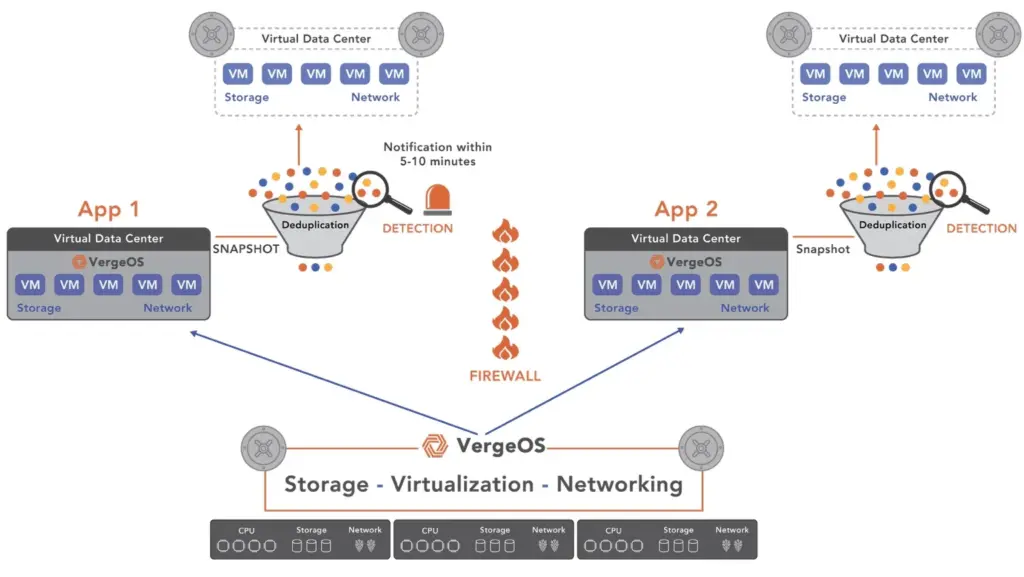
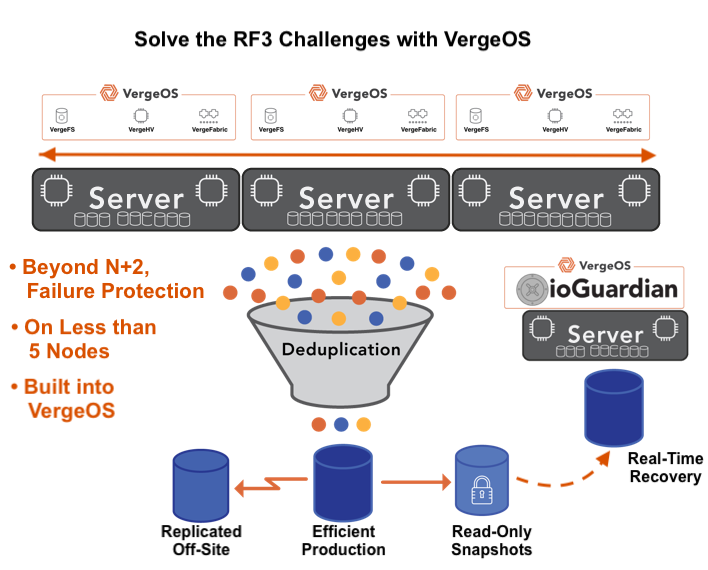
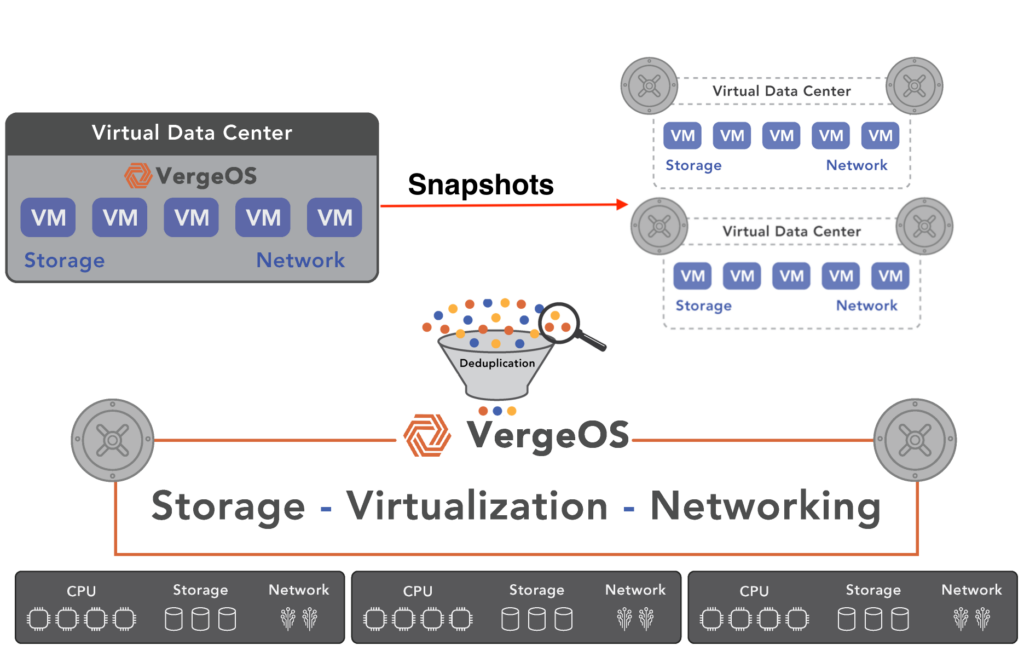
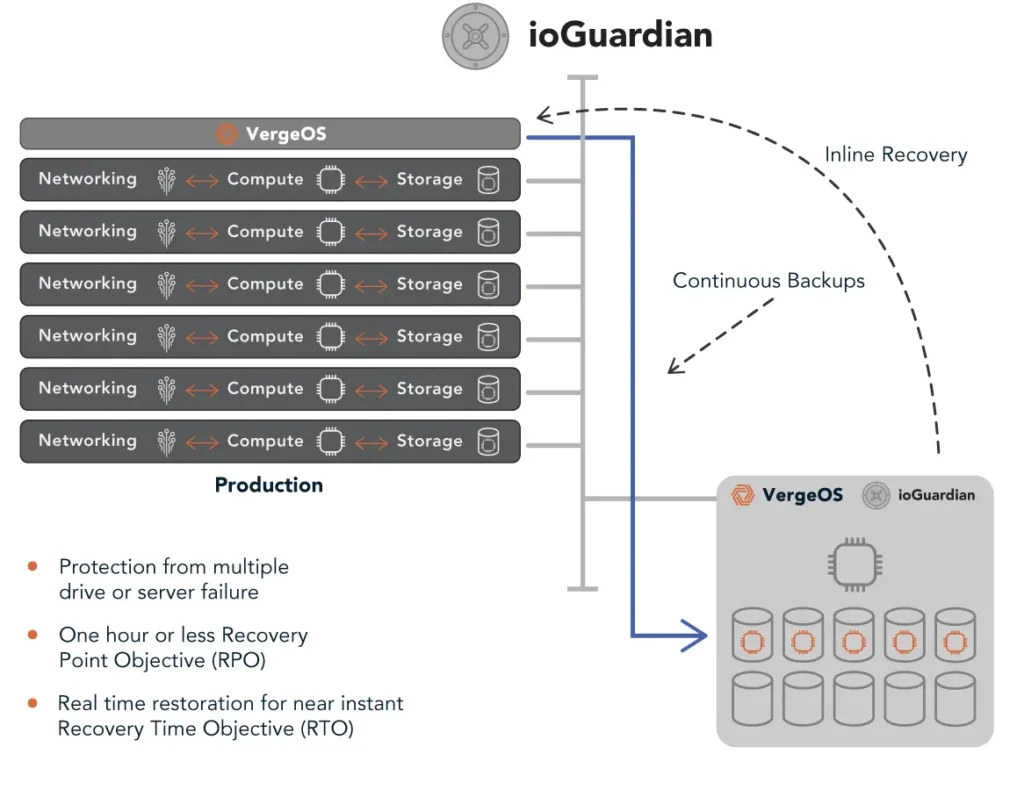
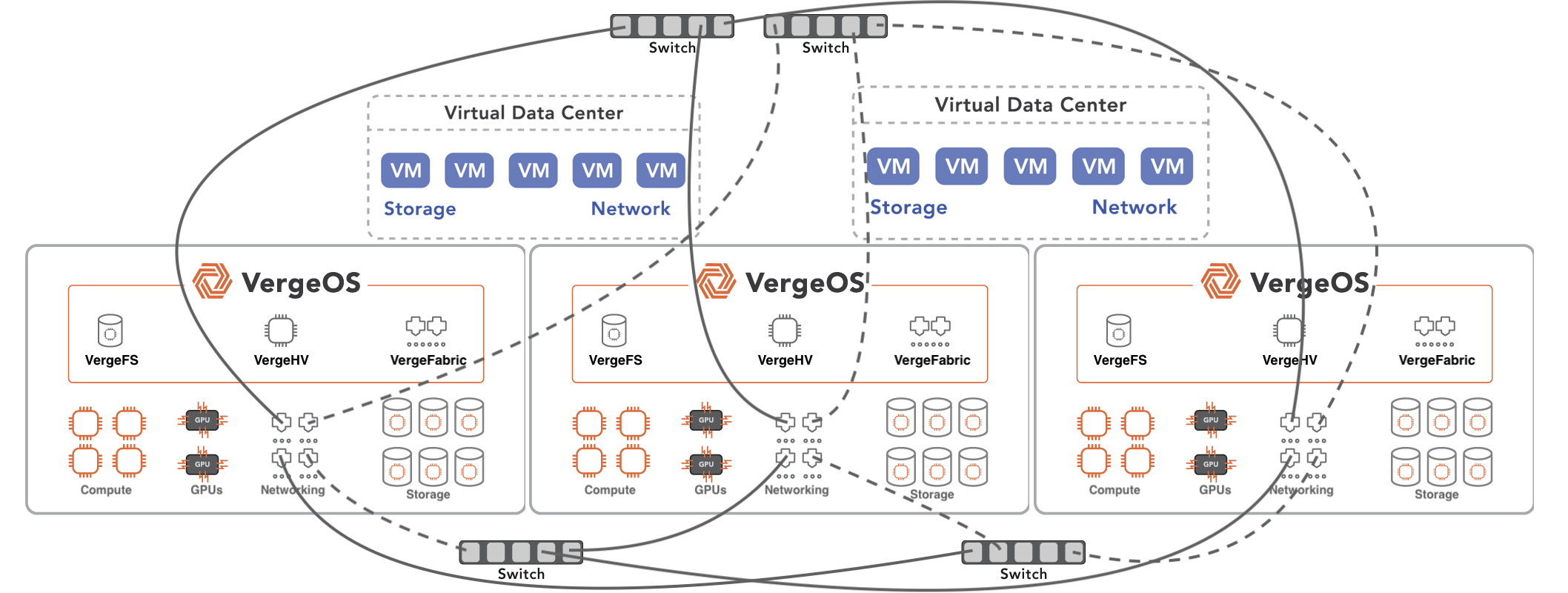
K–12 and municipal IT teams can simplify disaster recovery with VergeOS by eliminating the need for separate backup systems, orchestration tools, and dedicated DR sites. VergeOS enables cross-replication, supports routine testing, runs on existing hardware, and includes all DR capabilities—snapshots, replication, and recovery—in the core license. This reduces cost and complexity while improving resiliency with minimal overhead.