Seasoned IT professionals frequently advise against using snapshots to protect VMs because of the limitations in the snapshot methodology common in today’s storage systems and software solutions. However, VergeOS has a unique approach, thanks to its integrated, cohesive operating environment that redefines the role of snapshots in data protection, making them the go-to option when administrators need to recover data.
The Challenges of Using Snapshots to Protect VMs
Despite their potential to address up to 90% of non-hardware-related recovery scenarios, snapshots are one of the most underutilized features in data protection. The core issue with today’s snapshot technologies lies in the widespread use of the redirect-on-write snapshot management method. While an improvement over the outdated copy-on-write technique, redirect-on-write still has significant challenges, particularly in modern data frameworks.
Each redirected write increases storage system overhead, which leads to noticeable performance degradation as the number of active snapshots grows. To counteract this, storage systems often require additional memory and processing power, which drives up costs. Software-based solutions, such as those provided by VMware, lack this flexibility, resulting in significant performance impacts even with a few active snapshots.
Additionally, redirect-on-write snapshots heavily depend on the integrity of preceding snapshots and the original volume. If any of these elements fail, the entire snapshot becomes unusable. This limitation directly conflicts with the 3-2-1 backup rule, which mandates maintaining three separate copies of data on two storage systems, with one copy off-site.
Common Use Cases and the Untapped Potential of Snapshots
Due to traditional snapshots’ inherent limitations, organizations often limit their use, primarily utilizing them to feed backup software. Typically, a snapshot is taken, backed up, and then deleted. This restricted use prevents snapshots from reaching their full potential in data protection.
If the limitations of snapshots could be overcome, they could significantly enhance an organization’s ability to recover from minor data loss events and major disasters.
Snapshots offer several key advantages:
- Speed: Snapshots can be created in milliseconds.
- Minimal Capacity Impact: Snapshots can be retained almost indefinitely with negligible storage impact.
- Instant Recovery: Since data remains on the device, recovery is almost immediate.
VergeOS and ioClone Make Using Snapshots to Protect VMs a Reality
To unlock the full potential of snapshots, the technology must overcome traditional limitations and align with the 3-2-1 backup rule by providing:
- Independence
- Zero Performance Impact
- Transportability
- Long-Term Retention
- Single File Recovery
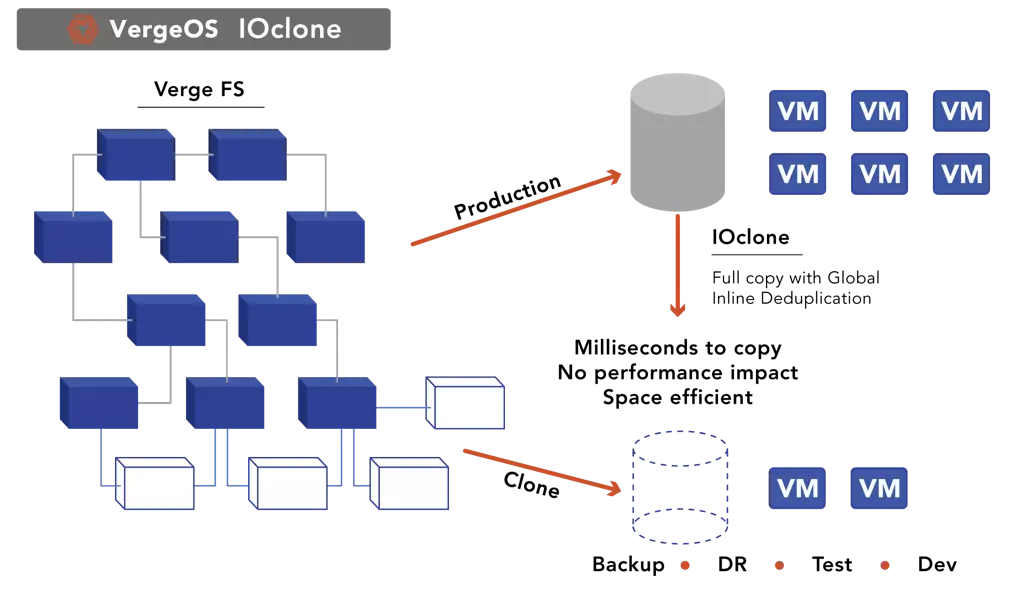
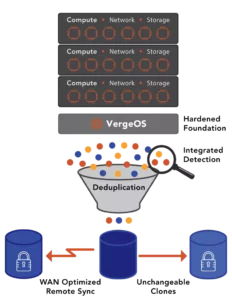
VergeOS has redefined snapshot technology with its innovative approach powered by IOclone. Unlike traditional snapshots that rely on the outdated redirect-on-write method, VergeOS uses IOclone technology to create complete, independent copies of selected objects (entire instances, virtual data centers, or virtual machines). VergeOS’s integrated deduplication ensures that these snapshots are instantly optimized, making the snapshot process as fast, if not faster, than traditional methods while consuming less overall capacity. VergeOS makes using snapshots to protect VMs a viable part of any data protection strategy.
This approach means VergeOS snapshots are independent of other snapshots and the original object being snapshotted. Even if the primary object is deleted, you can mount the snapshot of that object and continue operations without interruption. Additionally, you can maintain as many active snapshots as needed and keep them for years without impacting performance.
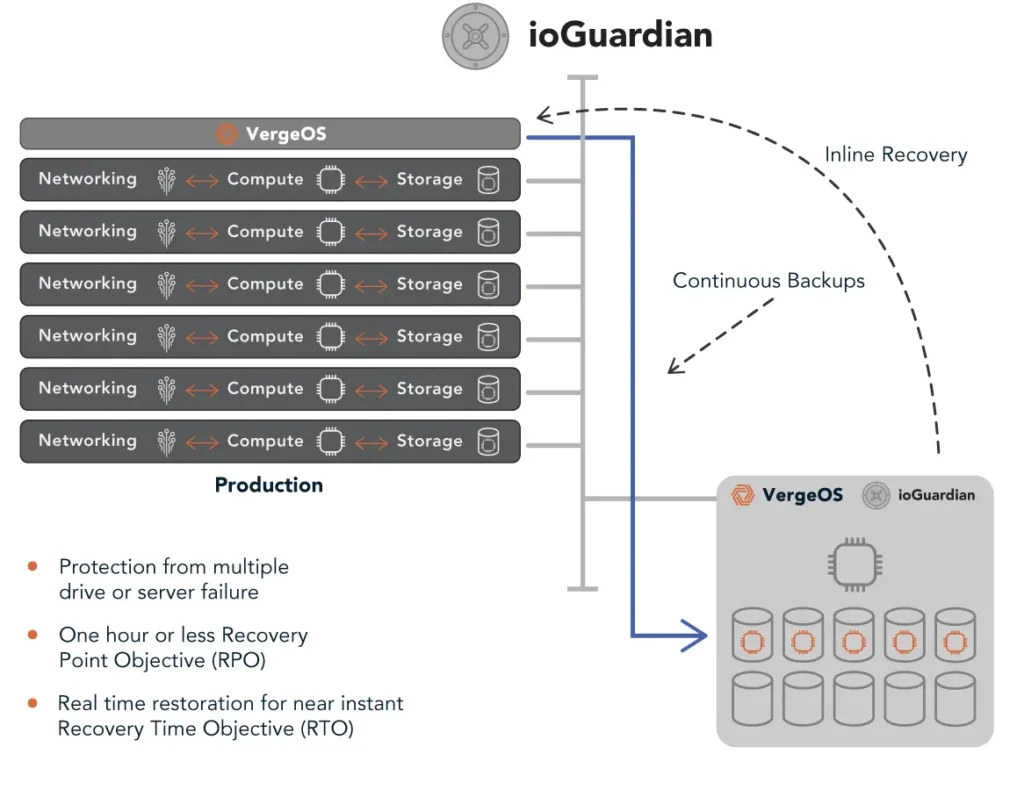
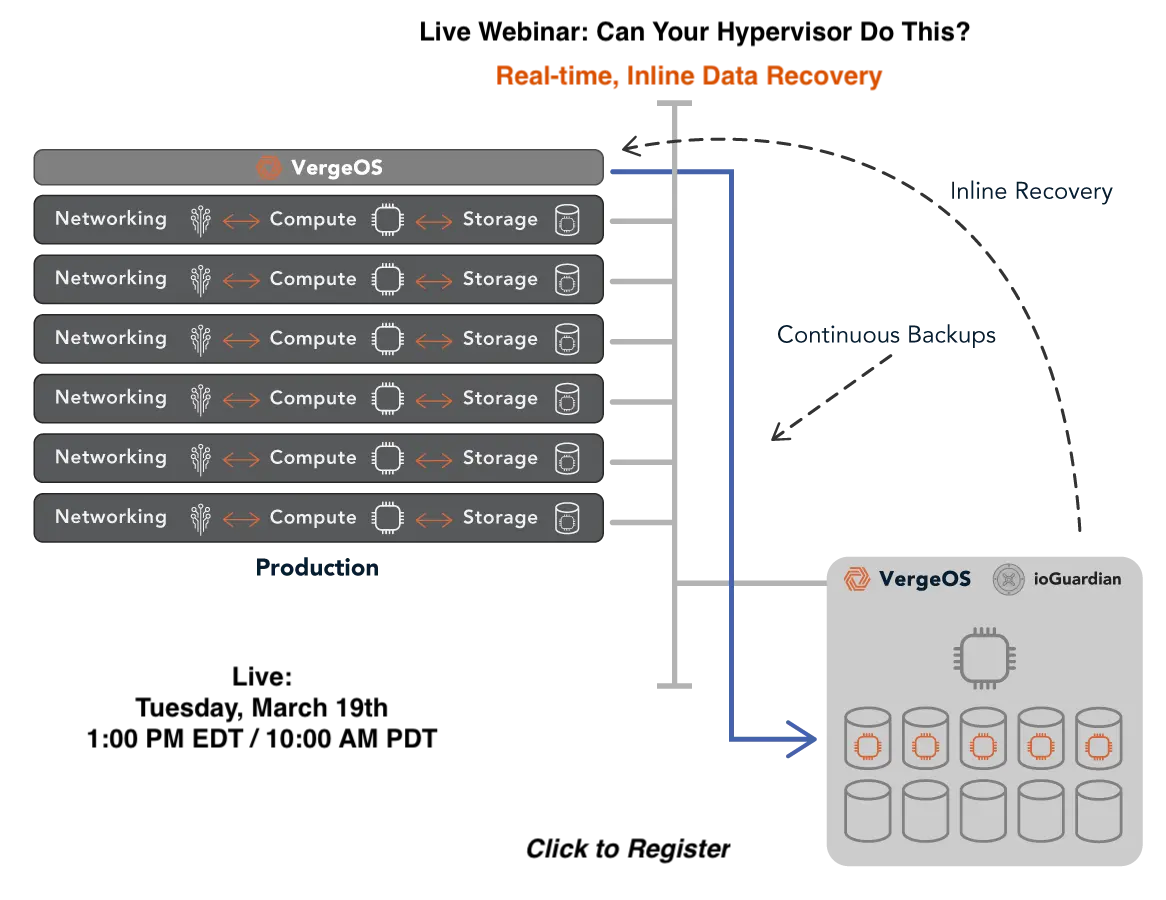
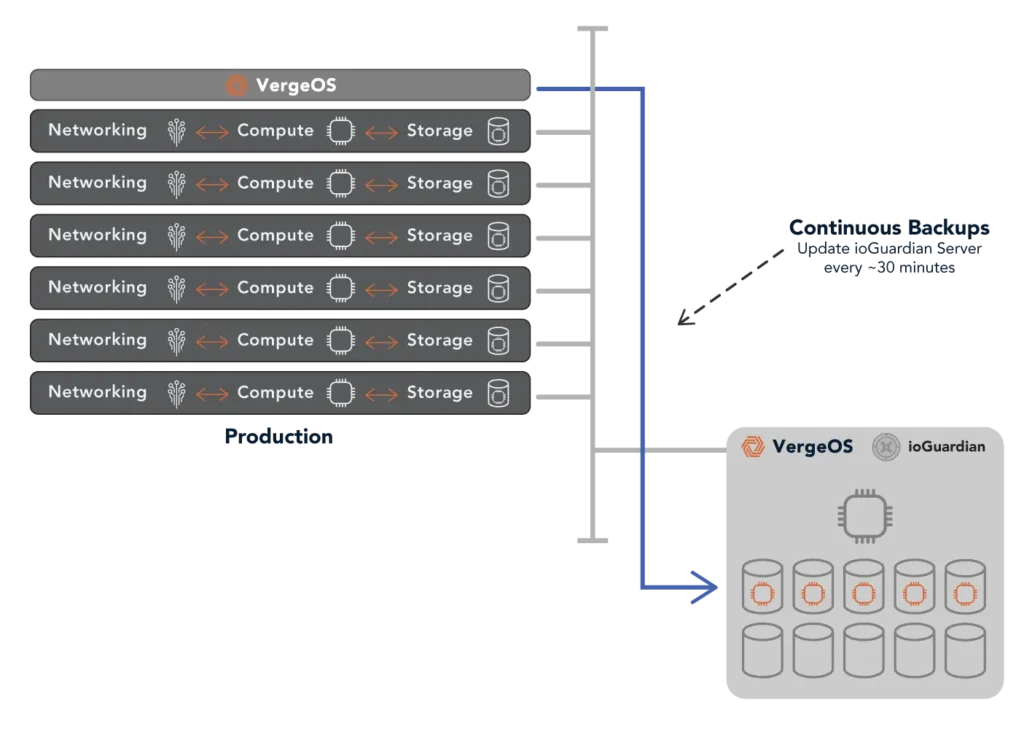
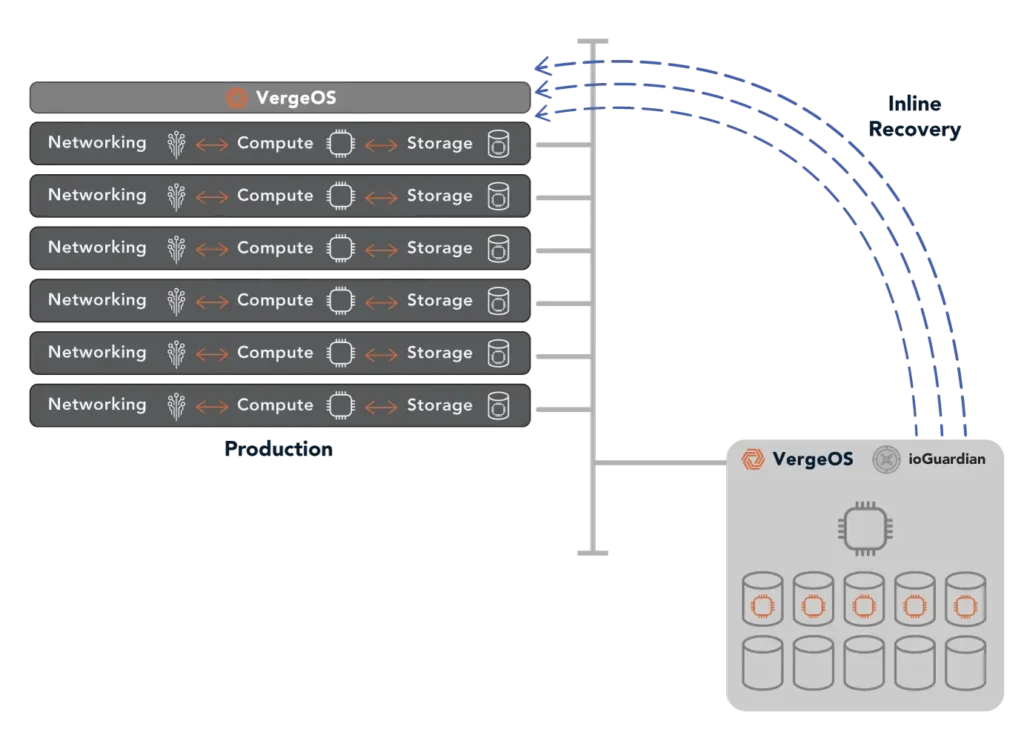
VergeOS’s ioGuardian, known for its real-time recovery capabilities, further enhances snapshot transportability. Because ioGuardian and VergeOS share the same deduplication algorithm, they work seamlessly together, allowing snapshots to be automatically pushed to the ioGuardian server for rapid updates and storage on a secondary in-data-center device. While most data centers back up once per night, VergeIO customers leveraging ioGuardian can create a full backup every hour without full backup capacity requirements.
These advanced snapshots, combined with VergeOS’s deduplication, also power ioReplicate for off-site data transfer. Independent snapshot schedules are supported on both ioGuardian and ioReplicate storage systems.
Finally, VergeOS snapshots provide robust single-file recovery capabilities. IT can easily mount a snapshot as a drive within a VM and copy the required file back to the production VM without any downtime. It’s a fast and straightforward process, but you don’t have to take our word for it. You can register for our latest hands-on lab to experience creating a VM, taking a snapshot, and recovering a file in action.
Conclusion
VergeOS transforms how organizations use snapshots to protect VMs by overcoming the limitations of traditional redirect-on-write snapshot technology. With features like IOclone, ioGuardian, and ioReplicate, VergeOS provides an independent, high-performing, and versatile snapshot solution ideal for using snapshots to protect VMs. This allows businesses to recover quickly from data loss events and ensures that their data protection strategies are robust and cost-effective.
If you are exploring a VMware alternative or planning a storage refresh, snapshots are just one of the many powerful features offered by VergeIO’s storage capabilities. VergeOS delivers a comprehensive suite of storage services integrated into VergeOS that are not only advanced but also highly cost-effective. Its integrated approach ensures that your infrastructure remains resilient, flexible, and ready to meet the demands of modern IT environments. Set up a whiteboard deep dive with me to learn how VergeOS can be your VMware Alternative or your next storage platform.
By integrating VergeOS into your IT infrastructure, you can maximize the benefits of snapshots and elevate your data protection to new heights while optimizing your storage strategy with a solution designed for the future.