Ransomware has emerged as a dominant threat to global businesses, but are backups enough for ransomware recovery? The most recent VergeIO study, “Top Concerns of VMware Customers,” showed that 25% of respondents faced a ransomware attack in the past year. Notably, every one of these victims had recently fortified their backup infrastructure, but the average time to recover from an attack was still over three weeks.
Backups: The Existing Safety Net Has Holes

Most organizations count on backup systems as a primary defense line, and every data protection vendor suggests that customers increase their spending on backup and recovery infrastructure. Even primary storage and infrastructure vendors like VMware are establishing relationships with data protection vendors to cover gaps in their product’s ransomware resiliency capabilities.
Despite all this, the VergeIO survey results, showing an average three-week recovery time suggest that this investment is for naught. Where is data protection falling short?
- Data Transfer Delays: Transferring data from backup to production storage is tedious and lengthens recovery periods.
- Lag in Ransomware Detection: Often, a user’s inability to access systems, not IT discovery, signals an attack, resulting in a three-day average detection time.
- Encrypted Backups: Delayed detection allows ransomware to compromise snapshots and backup copies, necessitating a manual, multi-phased recovery strategy.
Why is Backup Ransomware Recovery So Slow?
There are a lot of reasons why recovery from ransomware takes so long. Partly, it is the fundamental issue with backup data. When you need to recover from any event, be it drive failure, a site disaster, or ransomware, you must physically copy or move data from a backup storage device to a production storage device. The more data, the longer recovery takes.
The Detection Problem

Again, VergeIO’s survey revealed that detection is a significant challenge that negatively impacts data recovery during a cyber attack. The survey found that, on average, it takes organizations three days to realize they are under attack. Moreover, the attack notification method is unreliable, as it often relies on users calling IT and reporting that they cannot log into their system. This notification time lag highlights the need for organizations to find solutions that can better detect and notify IT of an attack. It seems unlikely that rapid detection can come from backup software.
The Impact of Slow Detection
If it takes three days to discover that ransomware encrypts files in your environment, it dramatically impacts recovery time. First, in most cases, because of poorly implemented snapshot technology, all snapshot data will contain encrypted data. Three-day detection also means that the backups, which are next in line, also have intermixed encrypted data.
While recovery from backup is likely possible, the backup copies need to be manually examined to understand what data on them has been encrypted and what data has not. The result is these customers had to do an “interleaved” recovery, which means IT is restoring some data from some backups and other data from other backups. This manual interleaved recovery is why it took the average customer over three weeks to recover data after the ransomware attack. 
Key Requirements for Rapid Ransomware Recovery
Identification Critical for Ransomware Recovery
To recover quickly from a ransomware attack, the first and most crucial step is to get notified about the attack as soon as possible. This will enable you to isolate the protected copies and shut down the network to prevent the attack from spreading. It also reduces the infiltration of the attack into backup copies.
Zero Data Movement Ransomware Recovery
The second requirement is to have more frequent backups of your data, which should be immutable and easily accessible. This way, you can move the copies into production without data movement, which can help you recover from the attack more efficiently. Most backup software solutions require you to copy data to a separate storage system for backup and then to even another for immutability.
VergeOS – Infrastructure-Wide Ransomware Recovery
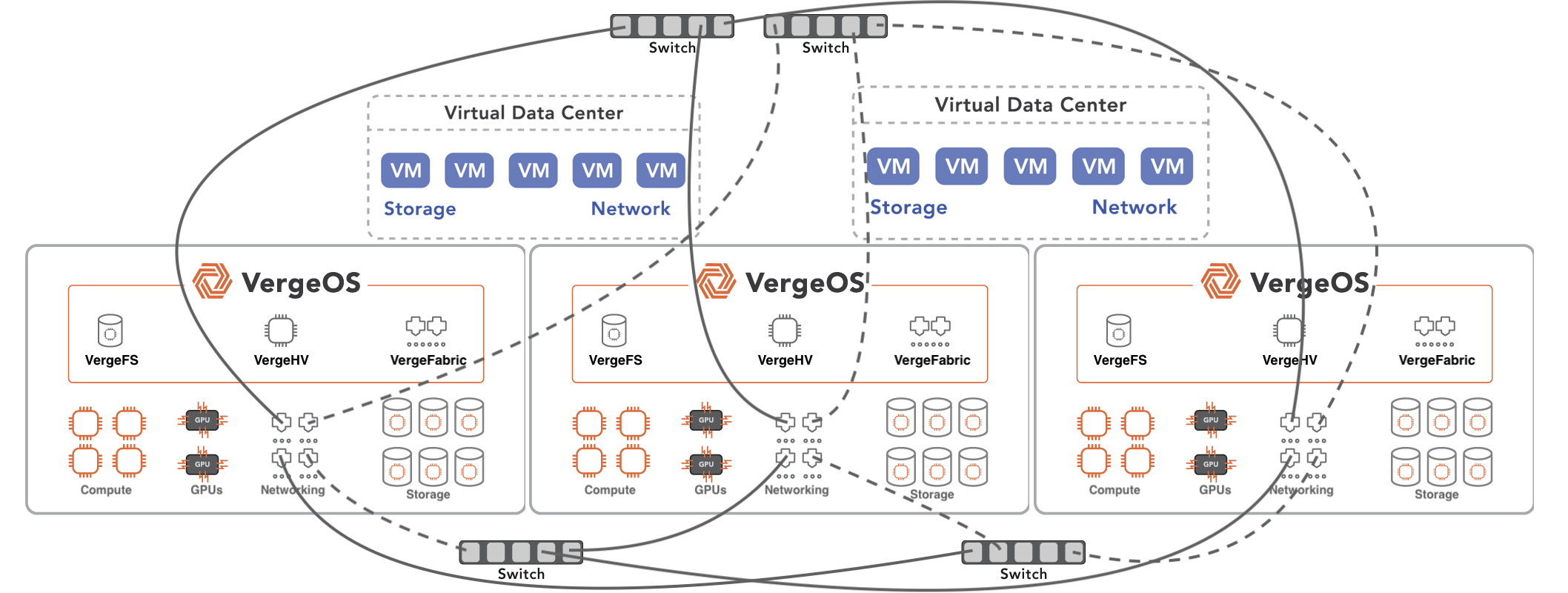
The VDC Foundation
To quickly recover from ransomware attacks with minimal, if any, data loss, it’s crucial to have a strong foundation. Our VergeOS solution uses Virtual Data Center (VDC) technology to provide this foundation. A VDC encapsulates an entire data center, much like a virtual machine (VM) encapsulates a physical server. Each VDC contains all the VMs, networking, and storage settings required for its workload or group.
VDCs can be easily moved, making them ideal for disaster recovery and specifically for ransomware recovery. For best results, IT departments should create multiple VDCs within their physical data center, each dedicated to a specific application, line of business, division, or customer.
Once the VDCs are created, a read-write copy of VergeOS is injected into each VDC from a read-only core copy. This protects the operating environment from any attack. In the unlikely event of an attack on the VergeOS instance within the VDC, customers can refresh it, and the read-only core will inject a new, clean copy of the OS into the VDC, thereby eliminating any contamination.
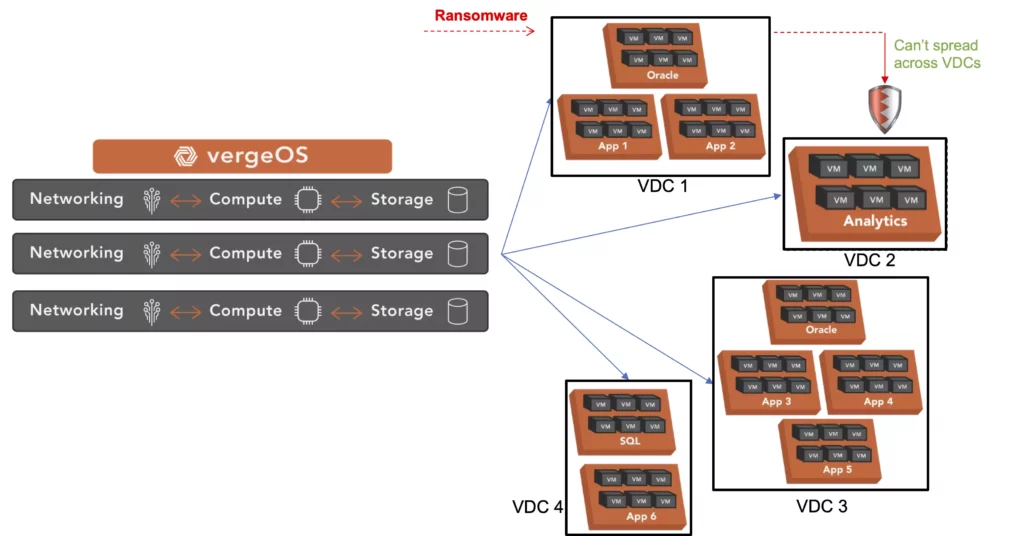
Moreover, VDCs provide additional value in the more common case of an attack at the application or file system level. Each VDC is an independent “walled garden”, making it nearly impossible for any malware to spread between virtual data centers. Lastly, VDCs make it easy for IT to test patching, as entire VDCs can be cloned in milliseconds.
VDC cloning enables IT to create a “lab” version of each VDC and apply patches to them first. IT can ensure that the patches work and don’t conflict before applying them to the production VDC. As we discuss in our article, “Ransomware Counts on Patch Tuesday,” applying patches quickly and securely is a critical aspect of a ransomware recovery plan.
Rapid Detection and Response
The VergeOS ransomware recovery capabilities enable customers to recover from an attack quickly with minimal data loss. First, VergeOS provides rapid detection using its IOfortify technology. Because VergeOS’s file system is built using a blockchain-like technology, it can quickly identify encrypted data. IOfortify, by monitoring unexpected spikes in new data creation, can pinpoint potential ransomware breaches in just 10 to 15 minutes.
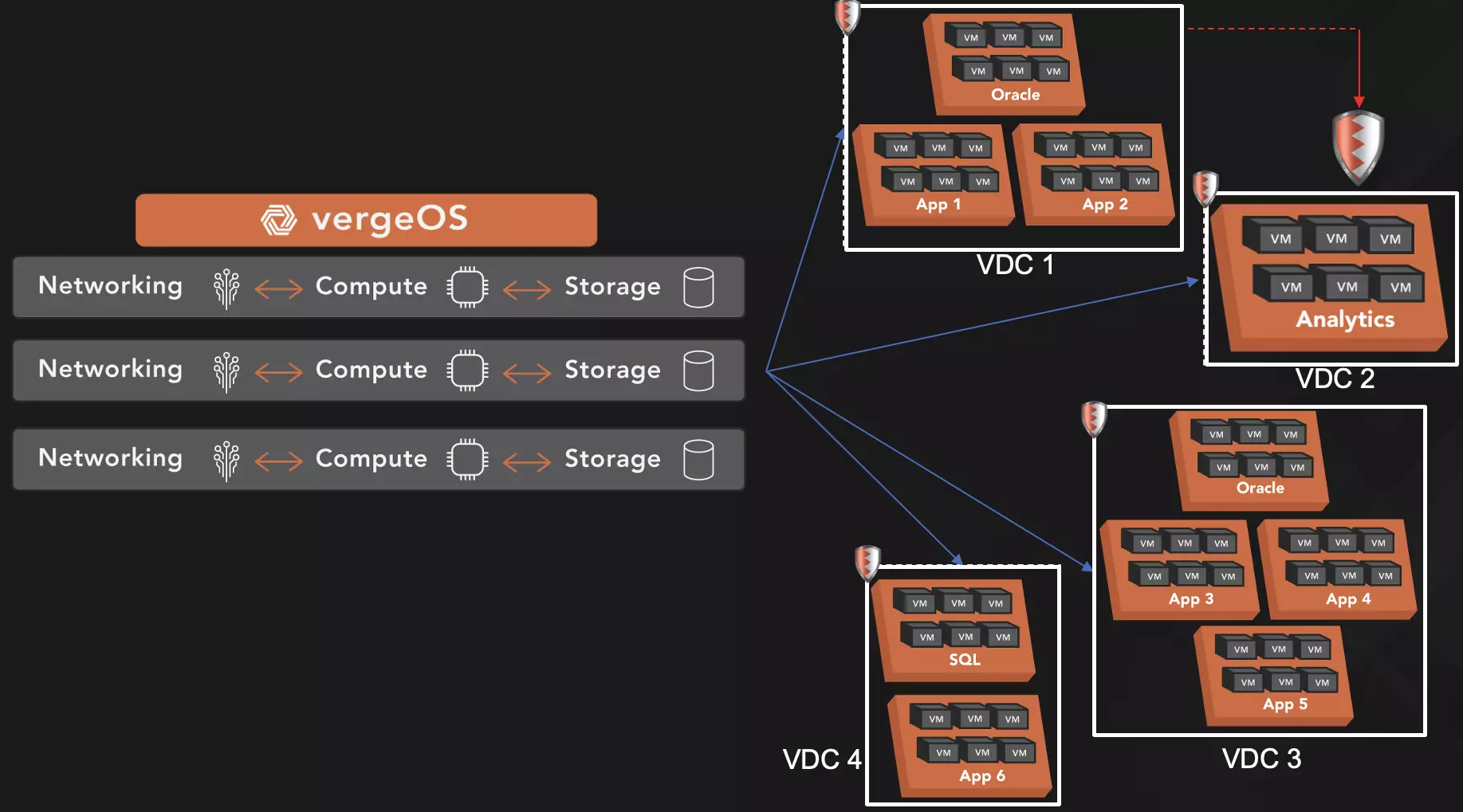
Next, VergeOS’s IOclone-powered snapshots are inline deduplicated copies that can be created within milliseconds, multiple times per hour. These clone-like snapshots don’t impact performance no matter how many there are or how frequently they are taken. Most importantly, they are also immutable, meaning malware can’t change them. These snapshots can also be replicated cost-effectively to a disaster recovery site, fulfilling the 3-2-1 rule of backup.
Once IOfortify notifies IT of an attack, they can resort to the most recent snapshot, which, while protected, likely has a copy of the undetonated malware file. However, VergeOS can mount those snapshots in a quarantined state and provide information as to which VMs were causing IOfortify’s anomaly detection to trigger. IT merely needs to scan the quarantined snapshot and remove the malware.
After cleaning, this minutes-old snapshot can be promoted to production, and without data movement, the customer is back in operation. The production copy can either be deleted, ensuring the complete elimination of the ransomware attack, or quarantined so that IT can study it further to understand how the attack got into the environment and spread. To learn more about developing a ransomware recovery strategy, download our white paper, “Creating an Infrastructure-Wide Ransomware Resiliency Strategy.”
Conclusion
Ransomware attacks have become a formidable challenge for global businesses. Attacks like the recent MGM incident, which took ten days, underscore the need for rapid recovery. Are backups enough for ransomware recovery? No, while backup infrastructure remains a line of defense, the disturbing three-week average recovery time underscores its limitations.
By employing a multi-pronged approach that includes rapid detection using blockchain-esque technologies, immutable IOclone-powered snapshots, and virtual data center encapsulation, VergeOS aims to reduce the vulnerabilities in the ransomware recovery process. As organizations continue improving their ransomware recovery capabilities, they must consider a more comprehensive, infrastructure-wide approach. VergeOS is the way forward by ensuring swift recovery and minimal data loss in the face of ransomware threats.