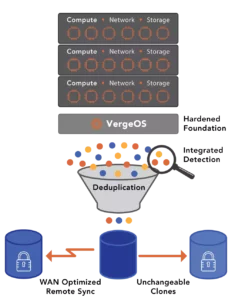
Ransomware recovery versus immutability is a critical consideration for organizations seeking to protect their data and ensure business continuity amid cyber threats. Immutable backups are not the sole solution to the ransomware threat. They are storage. Valuable, necessary, but still just storage. Treating them as the solution to ransomware recovery is like saying a vault prevents theft—it doesn’t. It only protects what’s inside, and only if you manage to get something valuable into it in the first place.
Recent industry commentary has implied that immutability alone neutralizes ransomware. That’s dangerously misleading. Immutable storage is one-third of the recovery equation. It’s not a recovery strategy, and it’s certainly not resilience.
True ransomware recovery depends on three elements working in concert:
- Frequent backup,
- Immutable storage
- Rapid, data center–wide recovery.
Miss any one of them, and you leave a gap large enough for attackers to exploit—and even if recovery eventually succeeds, it will be slow, costly, and operationally disruptive.
Frequent, Immutable Protection — Because Ransomware Doesn’t Wait for Your Schedule
Ransomware doesn’t strike politely during maintenance windows. It hits when you’re unprepared. The difference between losing a few minutes of data and losing an entire business day is measured in backup frequency.
Most IT shops still run daily or twice-daily backups—habits left over from tape systems that couldn’t do better. That schedule creates 12- to 24-hour exposure windows, during which ransomware runs free and undetected.
A financial services company experienced the ransomware recovery versus immutability firsthand during an incident. They scheduled immutable backups at midnight and noon. The attack started at 2 p.m., encrypting six hours of transaction data before detection. They flawlessly restored from the immutable backup, returning to the noon backup point, but lost six hours of verified transactions. Additionally, they faced a day of downtime while completing the full restore and manually rebuilding unprotected network and storage configuration settings. While the immutability feature proved effective, their schedule and process did not.
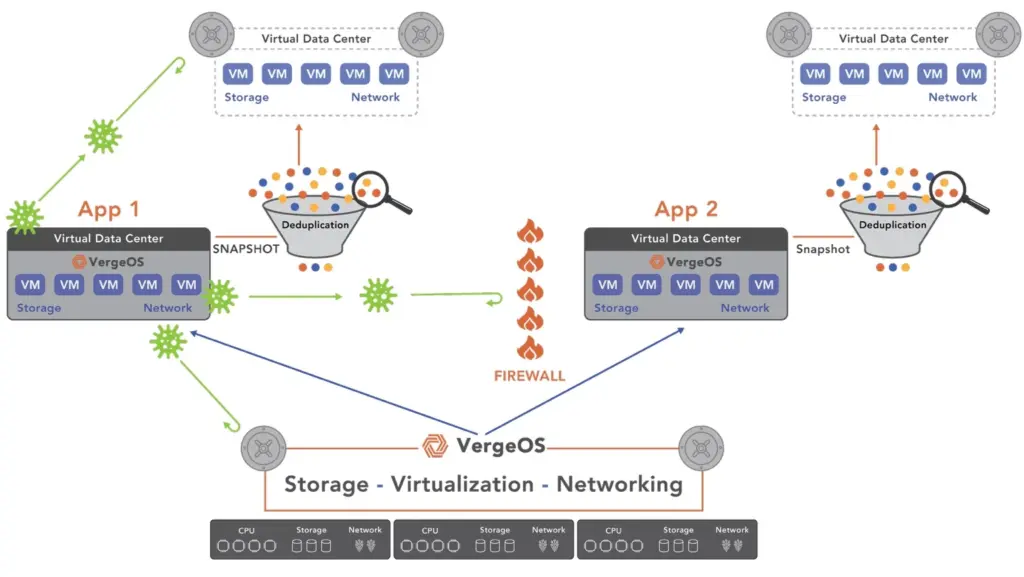
Modern infrastructure eliminates that trade-off. VergeOS provides infrastructure-level protection, creating immutable snapshots every hour without a performance penalty. This frequency provides a significant improvement in RPO.
The Downside of Immutable Protection
Immutability backup is essential, but it isn’t without challenges. The same protection that prevents deletion also prevents cleanup. If your storage pool runs out of space, you can’t purge old immutable backups until their retention policies expire. Keeping one long-term immutable backup makes sense for compliance, but for ongoing operations, organizations need a blend of rapid, short-lived immutable backups and read-only operational snapshots that can be rotated frequently.
Two problems emerge. First, most immutable storage systems can’t sustain frequent backups—they rely on traditional backups that must later be transferred to immutable storage, adding time, complexity, and duplication. Second, this delayed immutability undermines recovery speed and increases the exposure window by separating protection from production.
VergeOS solves both problems. It supports immutable and read-only snapshots simultaneously, enabling near-continuous protection without bottlenecks. Administrators can define short-term, immutable snapshots for ransomware defense and operational read-only snapshots for daily continuity, maintaining a balance between performance and capacity.
Immutable Protection IS Necessary
Attackers don’t just encrypt data. They steal credentials. They script the deletion of your backups before the encryption even starts.
That’s why immutable storage is essential—but only if it’s implemented correctly. Traditional backup systems depend on the integrity of credentials. Admins can delete or alter backups at will, which means attackers with admin credentials can, too. That’s not security. That’s wishful thinking.
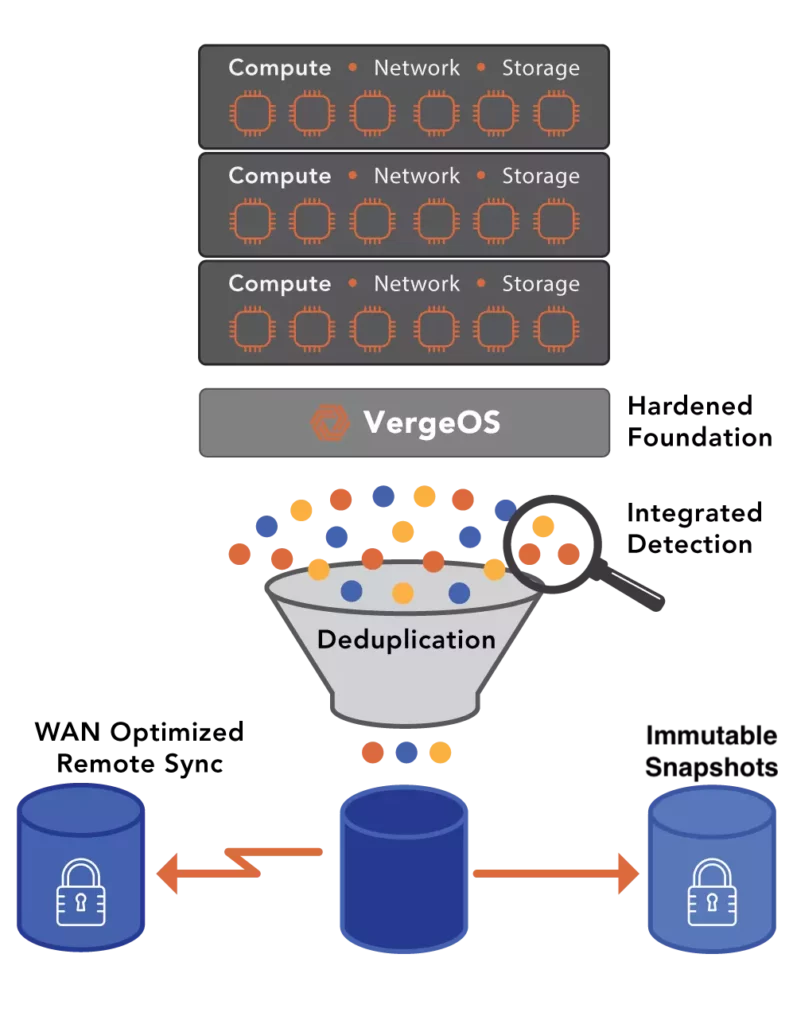
VergeOS eliminates that dependency. Once created, an immutable snapshot cannot be deleted or modified until its retention policy expires. Not by an administrator. Not by a domain admin. Compromised credentials make no difference. The infrastructure-integrated snapshots remain untouched and serve as the foundation for full recovery.
And this is the point most “immutability solves ransomware” advocates miss: immutability that lives outside your production environment introduces risk. External immutable storage adds latency, dependency, and cost. Data has to travel across networks to reach protection, then travel back for recovery. That’s the time you don’t have when recovering from an attack.
Immutable Protection – Head-to-Head Comparison
Ransomware recovery versus immutability backup must factor in the total time to recover, not just that the data is stored in an immutable state. Recovering from an external object store requires three things before a VM is usable: the source must read and rehydrate deduplicated chunks, the network must carry the full logical data, and the all-flash target must ingest and, often, run inline deduplication. The slowest stage determines the elapsed time. A simple way to express it is:
Time = Logical bytes to restore ÷ Sustained end-to-end throughput.
On a 10 GbE path, wire rate is 10 Gbit/s = 1.25 GB/s. Real payload after protocol overhead typically lands in the 0.9–1.1 GB/s range. Using 0.9 GB/s as a realistic single-link figure, a 100 TB restore is:
100 TB ≈ 100,000 GB ÷ 0.9 GB/s ≈ 111,111 s ≈ 31 hours.
That represents the best case when the source can continuously feed the link.
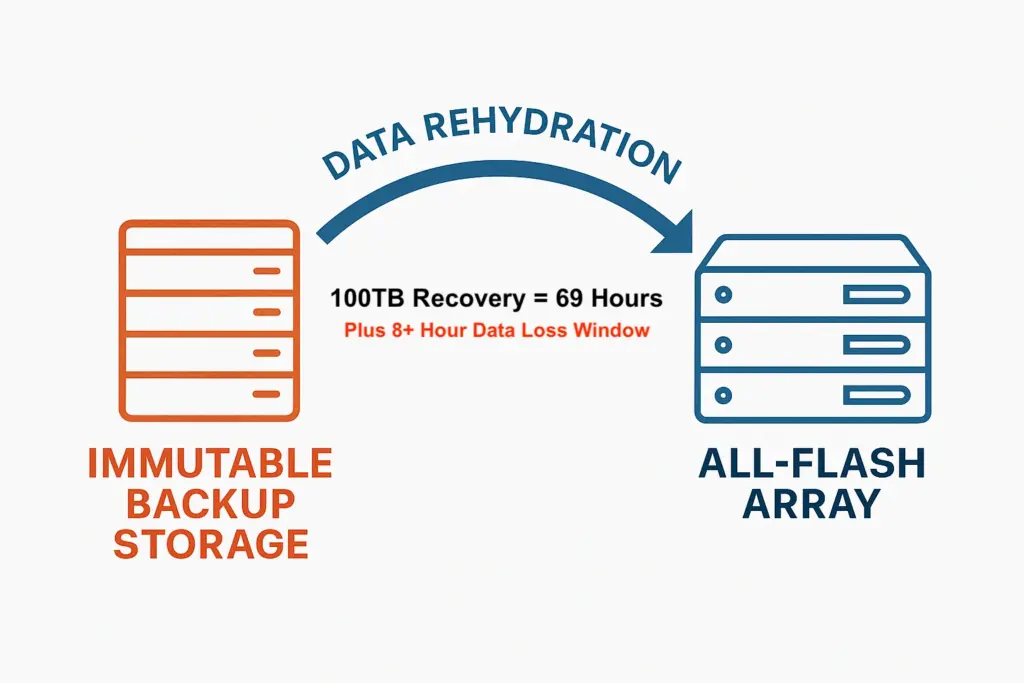
In practice, a deduplicated HDD source must rehydrate chunks, which means it performs many small, random reads and index lookups. Spinning disks handle that poorly, so sustained rates often fall to 0.6 GB/s or less. At that rate, 100 TB ÷ 0.6 GB/s ≈ 166,667 s, or 46 hours. If rehydration drops further to 0.4 GB/s due to seek-bound disks or cold indexes, the same job stretches to ~69 hours. The all-flash target’s inline deduplication adds a small amount of CPU work but rarely becomes the bottleneck on a single 10 GbE stream.
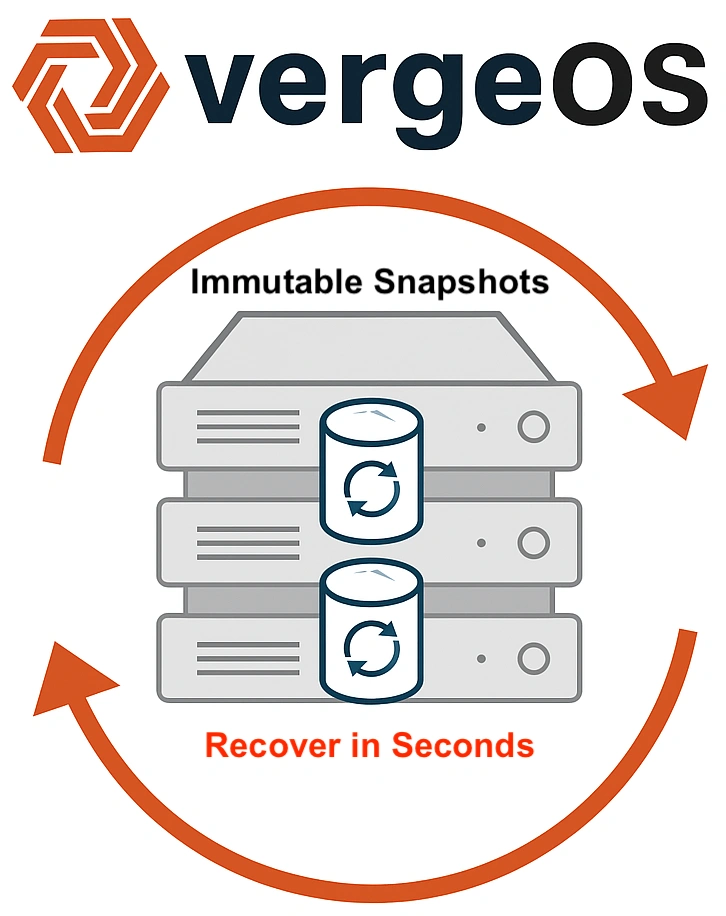
With VergeOS snapshots, immutability is integrated directly into the infrastructure. There are no external targets and no data transfers. Recovery simply re-references existing deduplicated blocks and advances metadata to a known-good point. There’s no rehydration stage and no bulk restore across the network. The operation primarily involves metadata manipulation and completes in seconds, even in a 100 TB (or 100PB) environment.
Both methods provide immutable recovery points, but only VergeOS snapshots deliver operational resilience. By eliminating data movement and rehydration, VergeOS removes the slowest steps from the recovery process—turning a 31–69 hour restore into an instant return to operation.
Data Center–Wide Recovery — Because Ransomware Doesn’t Attack VMs, It Attacks Environments
Ransomware rarely stops at a single system. It moves laterally, encrypting application servers, databases, file shares, and authentication layers. Typical attacks touch dozens to hundreds of VMs across interdependent workloads. Restoring them one by one isn’t recovery—it’s triage.
Most backup tools still treat VMs as isolated entities: pick a VM, select a point in time, restore, reconfigure, and hope it connects. That works for a disk failure, not a data center compromise.
This piecemeal approach produces inconsistency. The database restores to midnight, the app server to 6 a.m., the file server to 3 a.m. They all start—but none agree. Logs reference transactions that no longer exist. Configuration files point to data that isn’t there. The environment boots but fails operationally.
A manufacturer learned that a ransomware recovery versus immutability focus can learned that moving the data back in position is only a part of the recovery effort. After restoring 140 VMs over four days following an attack they realized the environment came online but didn’t work. Database schemas didn’t match application versions. Systems pointed to the wrong shares. It took another week to reconcile data and configuration mismatches. They recovered VMs, not a business.
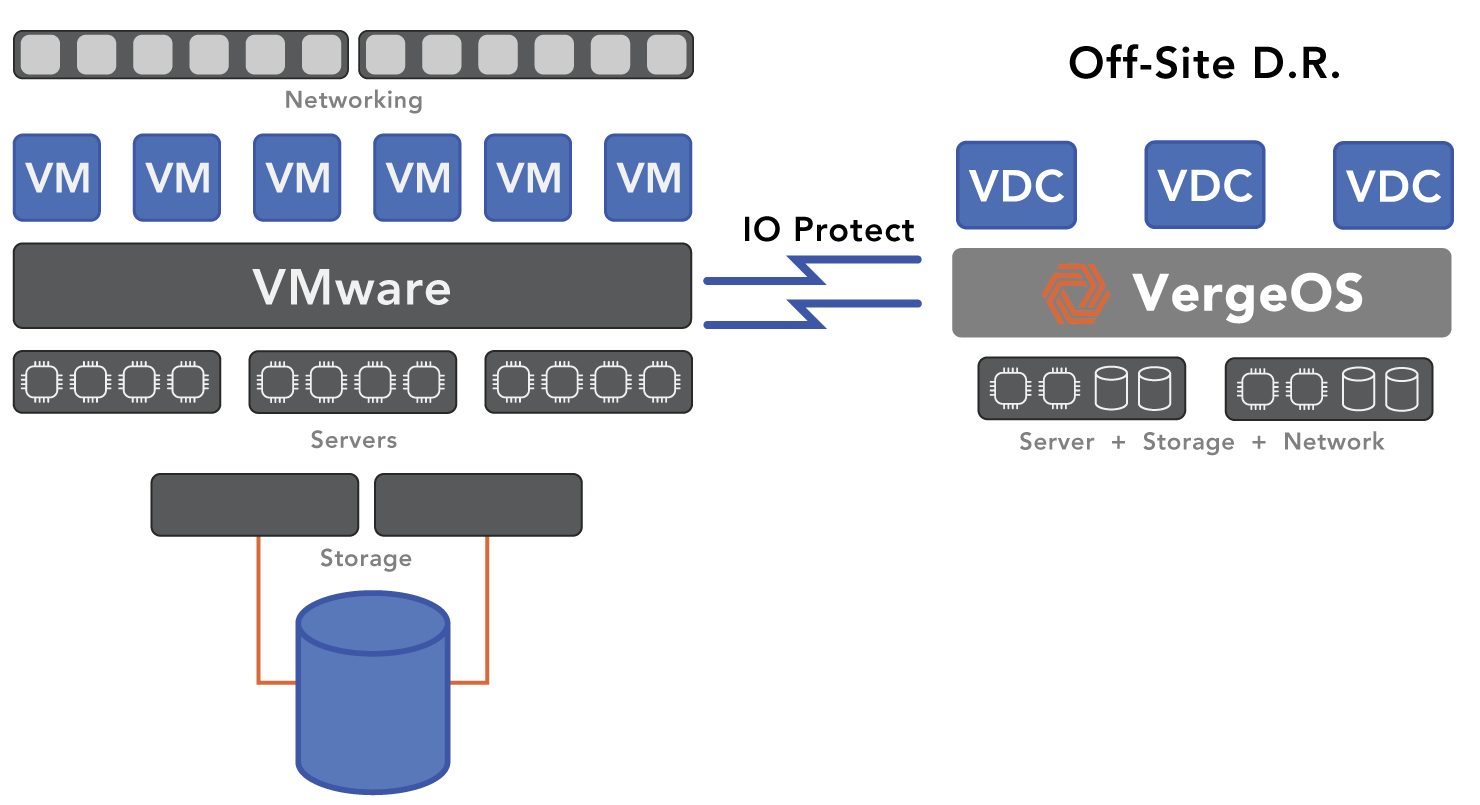
VergeOS avoids this through Virtual Data Centers (VDCs)—self-contained environments that encapsulate compute, storage, networking, and security policies. A VDC restores as a unit. One operation brings back the entire environment—every VM, every dependency, every policy—all synchronized to the same moment in time.
That’s not just recovery. That’s continuity.
A Final Word on “Ransomware’s Kryptonite”
Calling immutable backups ransomware’s kryptonite is like calling a safe a security system. It’s useful, but without detection, frequency, and the ability to rebuild what’s lost, it’s just a box of cold data. All immutable storage does not equal ransomware protection. Ransomware isn’t defeated by immutability—it’s defeated by recovery. Immutable storage buys you time; VergeOS gives you your business back.
Watch our Webinar on the latest version of VergeOS 26 to learn how to
- Exit VMware without disruption or licensing risk
- Repatriate workloads from costly public clouds
- Improve cyber resiliency through integrated architecture
- Prepare for AI by consolidating infrastructure into a unified platform