According to our recent survey, one of the requirements of any VMware alternative is to exit VMware without a server refresh. IT leaders are driving this requirement for three primary reasons:
- VMware’s latest versions force decommissioning server hardware long before it has outlived its applicable service.
- The quality and performance of server hardware built within the last five years suggest that it can reliably support workloads for up to ten years.
- Delaying or eliminating server refreshes is a great way to contend with flat budgets.
Why, then, does VMware require customers to upgrade to go through a server refresh so they can run the latest versions of their software? Why also do most VMware alternatives force you to buy prepackaged hardware bundles? The answers come down to efficiency and hardware dependency. Infrastructure software vendors with bloated code and strict server hardware requirements are forcing you into a lifetime of premature server refreshes.
Efficiency Eliminates Server Refreshes

Vendors force you into server refreshes to hide the inefficiencies in their code and the lack of foresight in design. Most infrastructure software is an assortment of different software applications, often from different vendors, that they attempt to “glue” together through a common management GUI.
VMware, for example, uses ESXi for the hypervisor, vSAN for the storage software, and NSX for the networking software. Each application has a different code base and overlapping code, which compounds VMware’s already significant virtualization tax.
As a result, there is a lot of redundant code and metadata in the infrastructure software and extra communication overhead to keep these separate applications in sync. The lack of integration between these applications creates significant overhead that impacts server performance and scalability.
Traditional Three-Tier Architectures don’t fare much better. Customers still face four to five-year refreshes for servers, plus they now add a separate refresh cycle for storage. There is also the unnecessarily high cost of a dedicated storage array.
Ransomware Makes It Worse
Our server also highlighted a significant concern about ransomware, and customers are constantly looking for solutions to give them an edge against the ever-evolving threat of having all of their data encrypted. In response, vendors constantly release patches to close down vulnerabilities in their code, releasing new software (for a fee) that keeps their older software safer. For example, VMware promotes NSX to help better protect ESXi. Instead of starting with secure infrastructure as a software core, they are bolting on potential fixes, which further impact performance and force customers into premature server refreshes.
According to our recent survey of almost 200 VMware customers, using existing hardware and improving ransomware protection were two of their top requirements for a VMware alternative. Join us for our live webinar tomorrow at 1:00 PM ET to learn the study results and see a live recovery from a ransomware attack. Register Now
Bundles Don’t Eliminate Server Refreshes
To hide continual software bloat, some vendors create predefined server bundles. These bundles use the latest processing power, which depends on specific CPU chip capabilities and fast NVMe flash drives to hide inefficiency, but they don’t eliminate server refreshes. They make server refreshes even more challenging. The customer still needs to refresh servers to provide enough power to compensate for the bloated software, but now they can only get that hardware from one or a tiny list of certified vendors. IT teams need to look no further than vSAN-Ready Nodes or Nutanix’s very restrictive hardware compatibility list as examples.
Turnkey HCI Makes it Worse
The turnkey bundle approach also makes a VMware Exit less appealing. Vendors that force the customer to buy new hardware as they are exiting VMware increase the costs of the exit dramatically. They also make installation more difficult because, at least for a while, the new hardware and the old must co-exist in the same data center.
VergeIO Eliminates Premature Server Refreshes
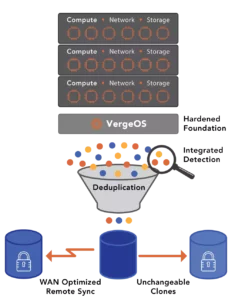
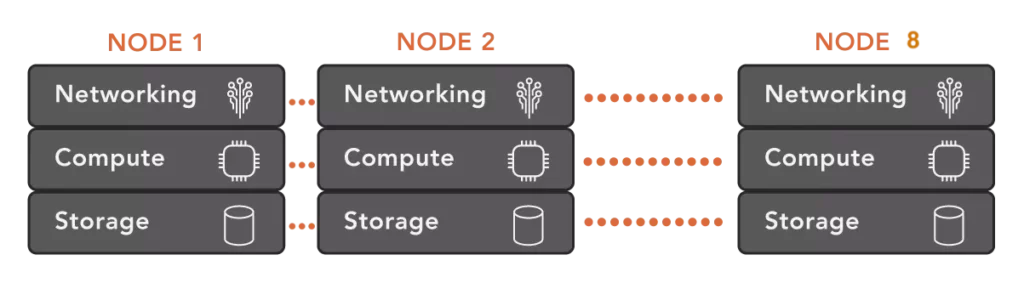
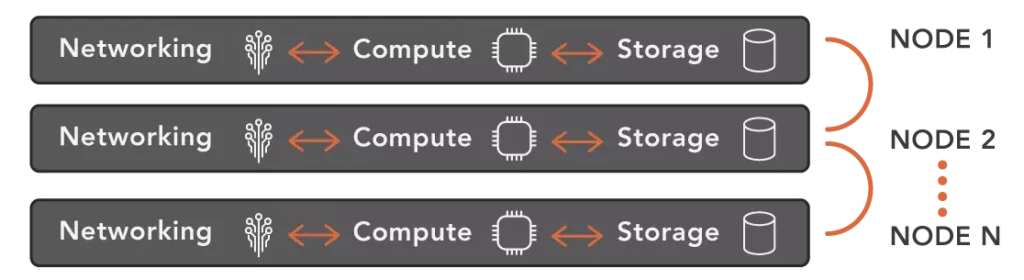
VergeIO unifies networking, virtualization, and storage software into a single software code base, eliminating the redundances common in other solutions. It also eliminates the extra and unnecessary lines of communication between the services, enabling a more scalable infrastructure.
Breathes New Life Into Existing Servers
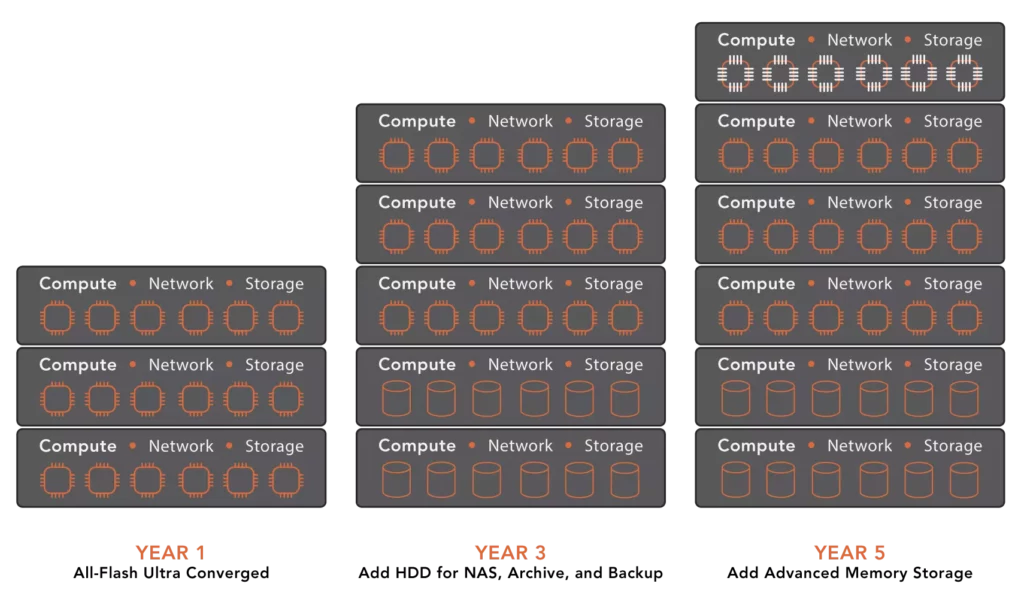
VergeOS does more than leverage existing hardware; its efficiency gives it a new lease on life. Our customers typically can increase overall virtual machine density and improve the performance of I/O intensive applications without resorting to an expensive dedicated storage array. Most VergeIO customers find they can delay or even eliminate the subsequent several server upgrades. When it does come time to add new servers to the infrastructure, add whatever brand and type of servers you’d like. VergeOS enables you to mix different server types within the same VergeOS instance.
Run Servers Until They Break
There is a common saying, “sweating the asset,” which means getting more than the typical four years from server and storage hardware. VergeOS enables customers to run the asset until it breaks permanently. Customers can do this because the entire infrastructure is redundant; VergeOS transitions VMs to surviving servers if a server fails. There is no extra charge for high availability (HA); VergeOS includes HA and all other features in every product edition. VergeIO has production customers running servers over six years old with no complaints about performance or fear of hardware failure. Those servers can co-exist with servers a few months old within the same instance. VergeOS eliminates server refreshes while maintaining availability.
Ransomware Resilient from Day One
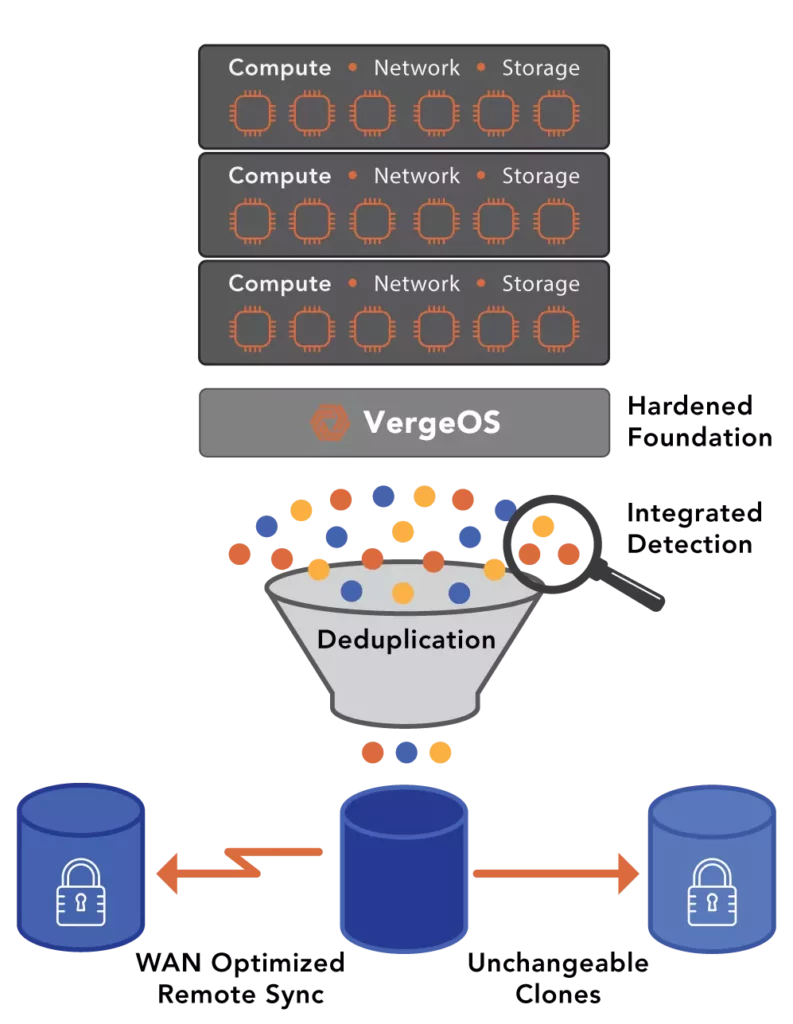
Ransomware resiliency is not an afterthought with VergeOS. As we discuss in our paper, “Creating an Infrastructure-Wide Ransomware Resiliency Strategy,” it is built into the core of our Utraconverged Infrastructure (UCI) platform. Our multi-layered, infrastructure-wide ransomware protection strategy includes the following:
- Virtual Data Centers (VDC) that enable customers to shrink the attack surface
- IOclone, which provides frequent, immutable snapshots without impacting performance
- IOfortify, which provides rapid detection of a potential attack and a hardened operating environment that acts as firmware, eliminating the potential of platform-level exploits.
Conclusion – Skip The Server Refresh
Exiting VMware without undergoing a server refresh is crucial for organizations looking to maximize their IT infrastructure efficiency and cost-effectiveness. VMware’s insistence on frequent server hardware upgrades and the challenges posed by ransomware threats have left many IT leaders seeking alternatives. However, most alternatives require new hardware and enforce restrictive hardware compatibility lists.
VergeIO enables you to exit VMware using your existing hardware, extracting more life from it while not compromising features or data resiliency.