
According to the ESG study, “Private AI, Virtualization, and Cloud: Transforming the Future of Infrastructure Modernization“, 72% of organizations experienced a cost increase in their infrastructure software, and 41% of those organizations are looking for a secure VMware Alternative. While reducing those licensing fees was the top priority, security ranked higher than concerns about migration complexity or the learning curve of adopting a new hypervisor platform.
With cyber threats intensifying, especially those targeting IT infrastructure, organizations are actively seeking infrastructure that delivers stronger defenses, simpler management, and enhanced operational control.
How VergeOS Responds
The VergeIO development team built VergeOS from the ground up to be secure by design. It reduces attack surfaces by collapsing multiple infrastructure layers—virtualization, storage, and networking—into a single software platform with centralized control. From licensing to workload isolation, VergeOS delivers the capabilities organizations expect from a secure VMware alternative.
To learn more about building a secure, resilient infrastructure and how to manage ransomware threats effectively, join us for our upcoming webinar, The Four Forces Accelerating Infrastructure Modernization, on Thursday, June 26, 2025, at 1:00 PM ET. Join ESG and VergeIO for an industry briefing on the state of IT infrastructure.
What Secure Virtualization Infrastructure Requires
To qualify as a secure alternative to VMware, the infrastructure must go beyond access controls and patch schedules; it must be architecturally designed to be secure.
Key Requirements for Secure Virtualization:
- Immutable Core: The infrastructure software must cryptographically verify its operating system (OS) and maintain it as read-only.
- RAM-Resident Execution: Runs from memory to prevent tampering.
- Integrated Recovery Paths: Support fast rollback to clean states in the event of compromise.
- Seamless Patch Updates: Organizations need regular updates to stay ahead of attackers; administrators must patch systems quickly, safely, and without disruption.
How VergeOS Implements Secure Virtualization
VergeOS boots into RAM using a read-only, cryptographically verified core image. This prevents unauthorized modifications and dramatically reduces the window for persistent threats. In the event of an attack, administrators can reload a known-good state in minutes—no reinstallation, no rehydration, and no downtime.
VergeOS also supports non-disruptive rolling updates, allowing organizations to patch their infrastructure without taking workloads offline. This keeps security current without introducing operational risk. As a result, 90% of VergeIO customers upgrade to the latest VergeOS version within 30 days of its availability—a proof point of both the platform’s reliability and the confidence customers have in its update process.
These are baseline features of a secure VMware alternative.
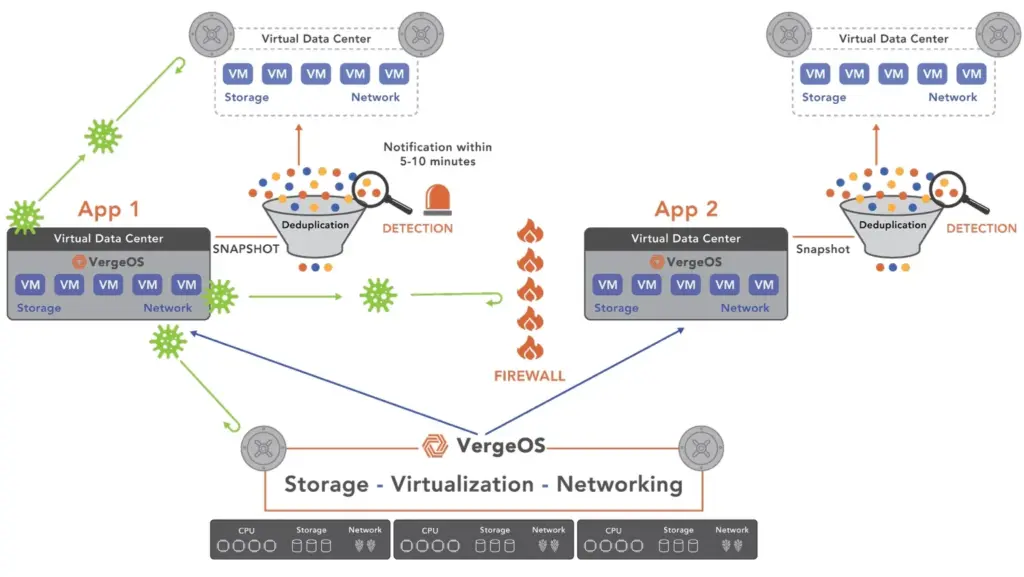
Secure Virtualization Requires Workload Isolation
Preventing lateral movement within infrastructure is just as important as securing the perimeter. VergeOS uses Virtual Data Centers (VDCs) to enforce strict boundaries between workloads.
Benefits of VDC-Based Isolation:
- Each VDC can include its own compute, storage, and networking settings
- Administrators can separate mission-critical applications from general user workloads
- A breach in one VDC does not expose the rest of the environment
How VergeOS Makes It Work
VergeOS enables IT teams to assign VDCs based on application, department, or compliance boundary. VergeOS isolates each VDC not only by policy but by resource scope and access control. This capability is foundational for delivering a secure VMware alternative that limits risk and supports compliance.
Secure Virtualization Requires Detection and Recovery
Even with the strongest defensive measures—such as firewalls, endpoint protection, and rigorous security training—ransomware attacks find their way into an organization’s infrastructure. This can occur through sophisticated social engineering attacks, zero-day exploits, compromised third-party vendors, or advanced persistent threats (APTs) designed to bypass traditional defenses.
When an attack inevitably slips through these safeguards, the organization needs an immediate and reliable recovery strategy to minimize operational disruption and data loss. Effective ransomware recovery is as essential as prevention, requiring tools that detect infiltration swiftly, isolate affected areas, and rapidly restore systems to a safe state.
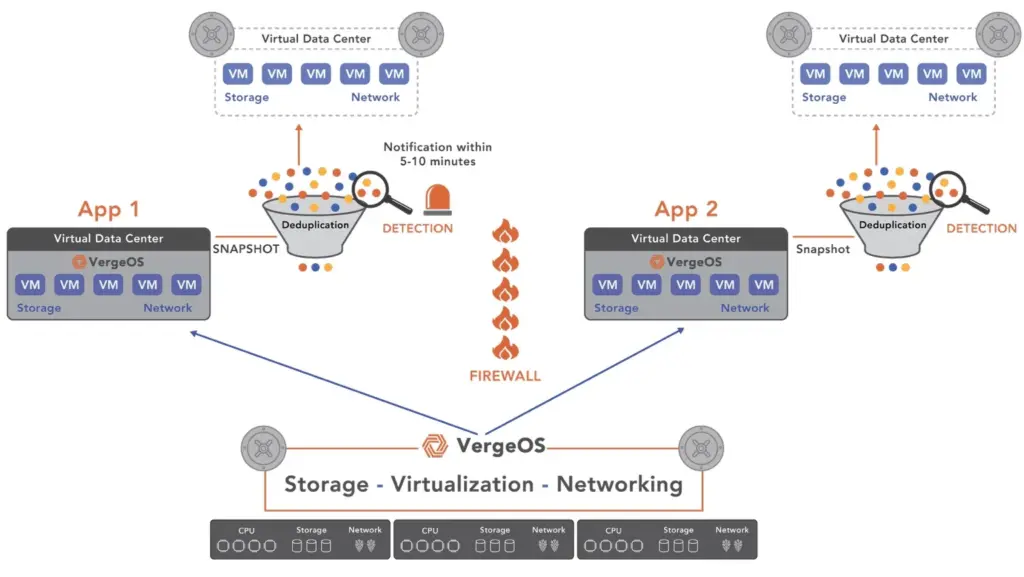
ioFortify: Early Detection through Deduplication Monitoring
VergeOS includes ioFortify, which continuously monitors deduplication efficiency. A sudden drop in deduplication is a warning sign of ransomware encryption. ioFortify alerts administrators early and recommends taking a snapshot of the environment before damage spreads.
VergeFS Snapshots: Fast, Clean Rollbacks
VergeOS’ ioClone technology enables read-only snapshots. Because of its integration into VergeOS, there is no limit on the number or the age of snapshots. VergeOS snapshots allow rapid rollback to clean, pre-attack states with minimal or no data loss and near-zero recovery time.
Together, ioClone, ioFortify, and Virtual Data Centers deliver what organizations expect from a secure VMware alternative: a ransomware-resilient architecture that combines early warning, data protection, and fast rollback.
Final Thoughts: Choose a VMware Alternative That Puts Security First
Weak security and vulnerability to ransomware represent significant infrastructure challenges. Organizations must adopt a comprehensive approach to address these issues. A secure VMware alternative can help achieve this goal. VergeOS provides a forward-thinking infrastructure platform that not only replaces VMware but also enhances the organization’s security posture.
If you’re evaluating VMware alternatives, ask:
- Was this platform built to survive an attack?
- Can it recover fast without introducing new risks?
- Does it give me more control with fewer add-ons?
VergeOS is a secure VMware alternative that protects what comes next. Schedule a technical whiteboard session and deep dive into our architecture.


